 XSS, Iframe injections and XMLHTTP post request errors on McAfee sites XSS, Iframe injections and XMLHTTP post request errors on McAfee sites
Written by [-TE-]-Methodman and DPSunday, 3 May 2009
I think it's not so easy :)
Methodman from Team-Elite (]['€AM€LiT€) has discovered a few vulnerabilities on several McAfee websites. Malicious users can exploit these bugs to infect customers and site visitors with malware, adware and spyware. They can also conduct phishing attacks by redirecting McAfee customers to fake McAfee sites. All bugs are still working and we hope that McAfee security people will fix them as soon as possible.
McAfee has been XSSed multiple times in the past and there has also been a long standing debate over the merits of (or lack thereof) McAfee's Hacker Safe seal (now McAfee Secure).
Server XMLHTTP post request errors
| Quote: |
msxml3.dll error '80004005'
A string literal was not closed. redirect[@org='www.mcafee.com/us/enterprise/solutions/network_access_'-->']<--
/error-pages/cls_redirect_lib.asp, line 67 |
|
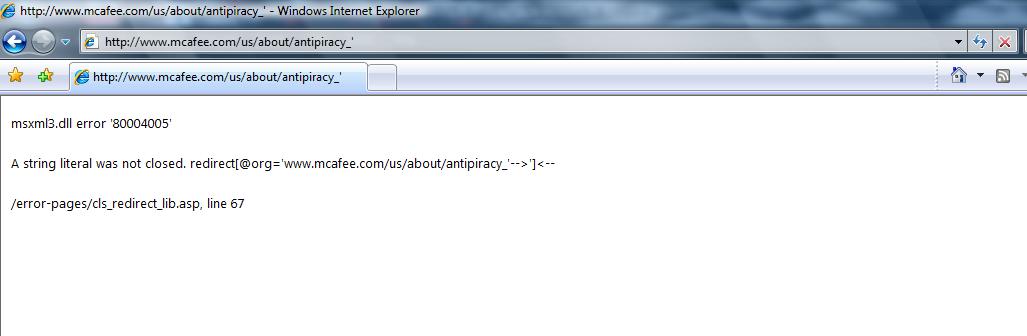
Iframe Injection
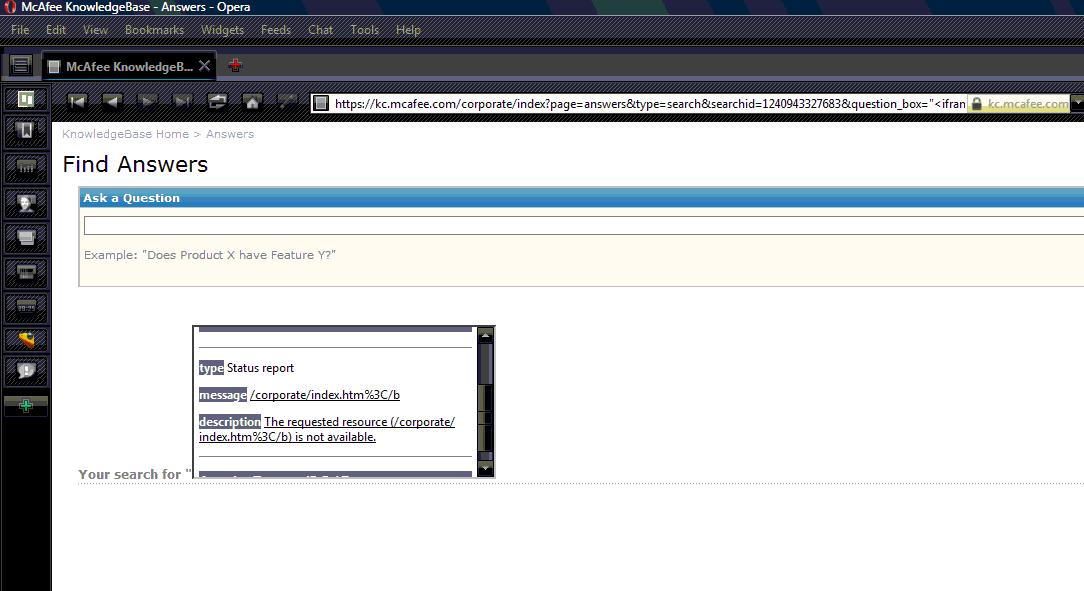
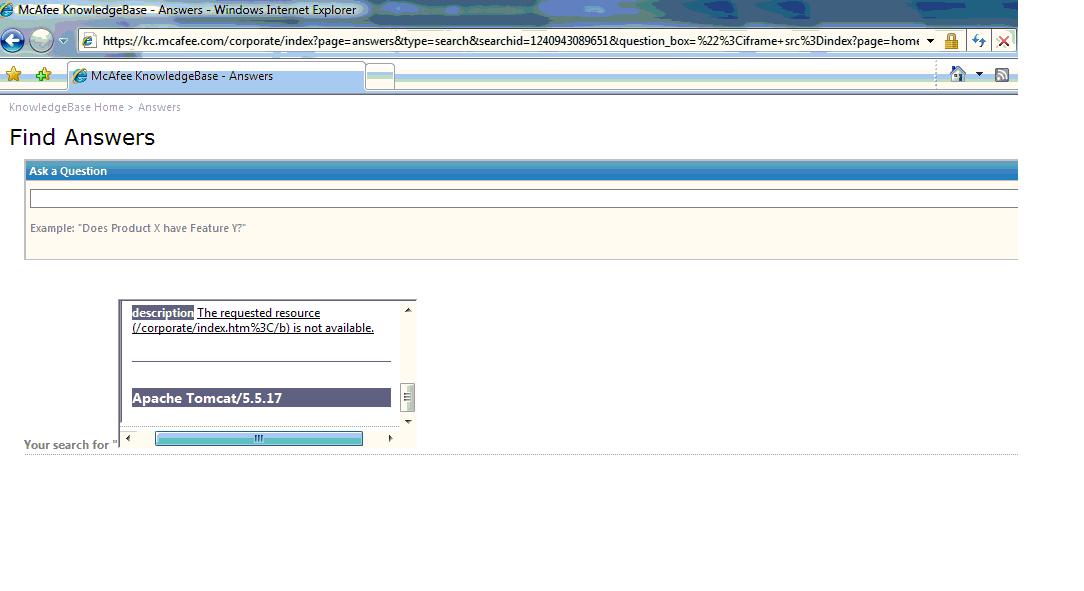
XSS and Iframe Injection
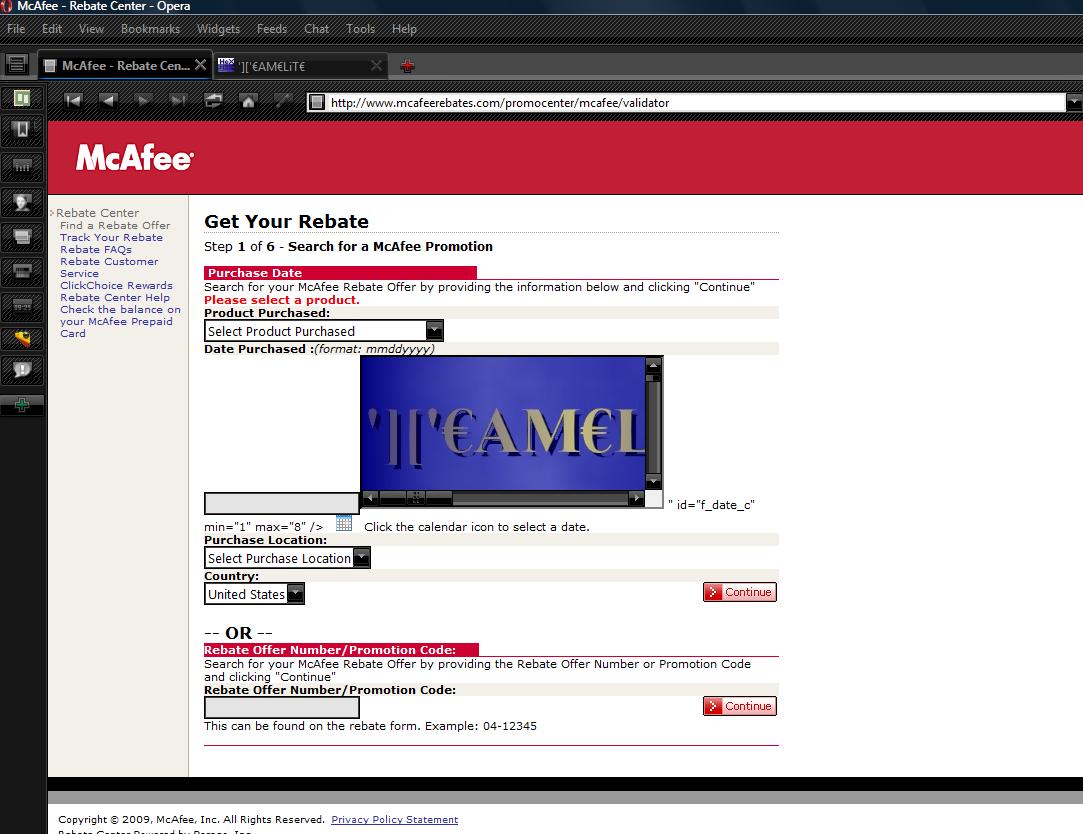
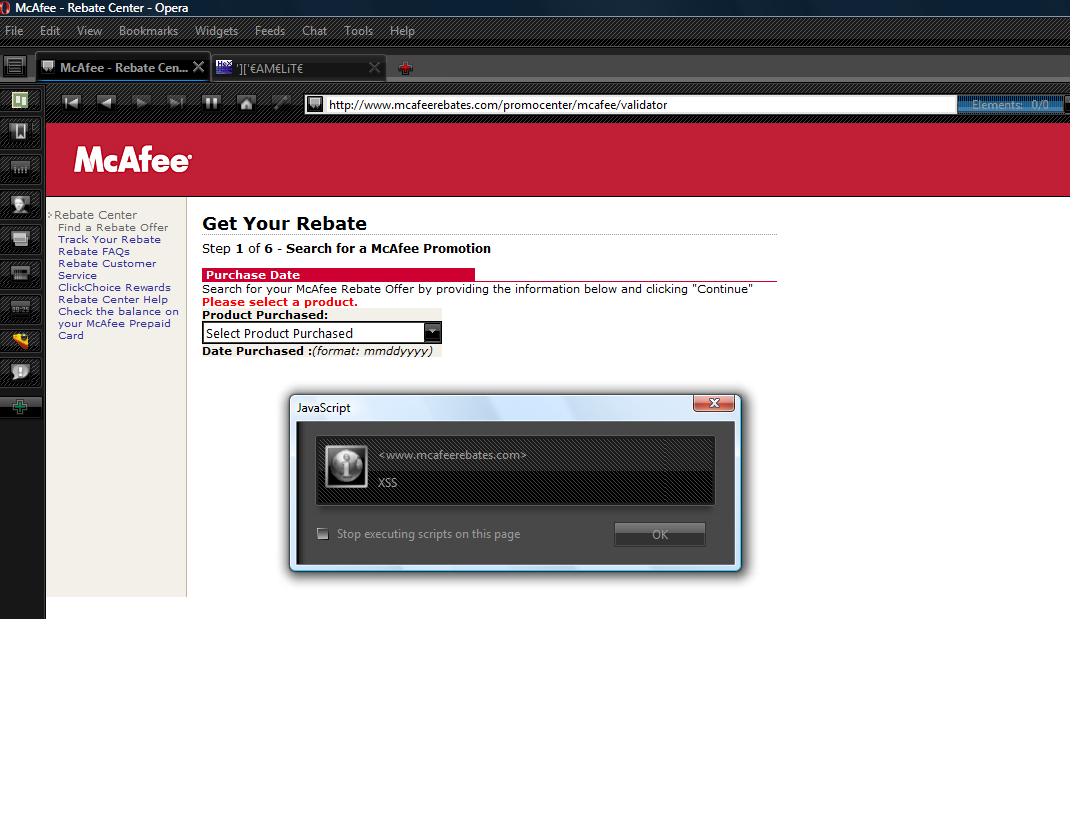
On the same website - http://www.mcafeerebates.com/promocenter/mcafee/promo_search.html - redirect also works fine
Example: - try to put something like this:
in Date Purchased or Rebate Offer Number/Promotion Code: and then click Continue.
You will be redirected to our website. :)
Original News: http://nemesis.te-home.net/News/20090501_Multiple_Bugs_on_Mcafee_Websites_.html
| 