 Microsoft leaves an open door to phishers! Microsoft leaves an open door to phishers!
Written by Giovanni Delvecchio, Zone-H.org
Wednesday, 11 April 2007Cyber criminals often appeal to users' unawareness and good faith to design their attacks, and in spite of constant information made by journals, blogs, magazines and IT Security organizations, this phenomenon, and specially the number of victims, keeps growing.
But what happens when a site considered as trusted, actually contains a “trap” for the user?
On this proposal, a “trap” has been discovered by Zone-H on MSN Video site, where it is possible to force the site through a crafted URL to display a web-page reporting the following message:
“This product requires Microsoft Internet Explorer 6 with Microsoft Media Player 10 and Macromedia Flash 6, or Mozilla Firefox 1.5 with Macromedia Flash 8, or Safari 2.0.4 with Macromedia Flash 8. To download these free software applications, click the links below and follow the on-screen instructions”..
“The Link Below”, whose the above text is referring to, can be set up (eventually coded in hexadecimal) by the attacker using the crafted URL.
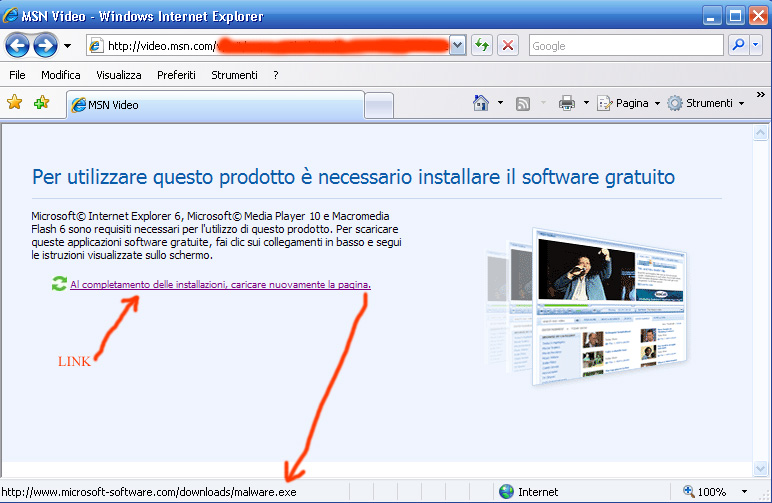
Similar situations represent a tricky risk for Internet users, since they could allow phisher and cyber criminals to build their attacks. Such attacks are particularly effective because they are based on the trusted relationship “User->Trusted Site”, since unaware users generally judge the authenticity of a web site on the basis of the address displayed on the address-bar.
But this is not the only problem affecting MSN, indeed, after further analyses we have discovered a Cross-Site Scripting vulnerability in the italian shopping section of MSN web site. In this specific case, it's easy to realize that the scope of malicious actions depends just on the attacker’s bravery.
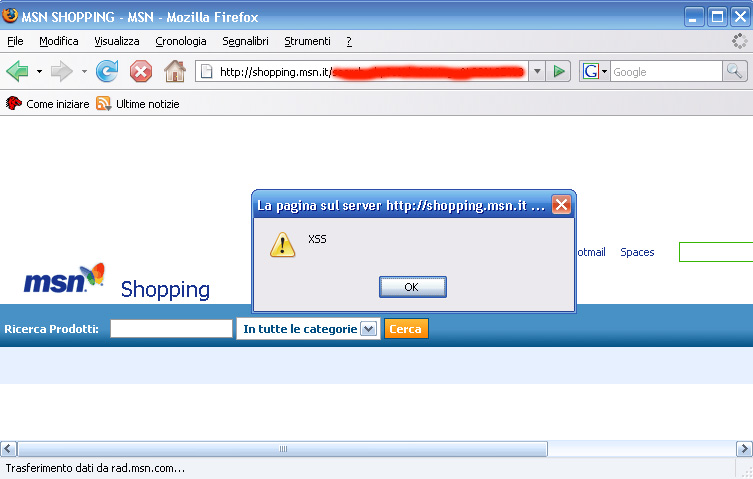
While waiting for Microsoft (already informed about the vulnerability) to fix the problems, we suggest to mitigate risks (for example when you have to do with e-mail, forum, chat, Instant Messagin, etc..) by using “ant-XSS” extension for own browser , and to check the content of the whole URL before clicking on it.
Indeed, links used as vectors for attack against websites affected by XSS and similar vulnerabilities, have a known pattern: almost in all cases, a part of the URL contains HTML tags like <script>, </script>, <img xsrc=javascript:..", which can be also “obfuscated” in hexadecimal (for example the tag “<script>” become “%3c%73%63%72%69%70%74%3e”) or they could hide other URLs that point to external websites.
Original News:
http://www.zone-h.org/content/view/14697/31/
| 