 Critical Ask.com frame redirect and XSS security issues Critical Ask.com frame redirect and XSS security issues
Written by DPWednesday, 2 June 2010
According to Alexa, Ask.com ranks 58th in the world. It is a highly popular search engine for web sites, images, news, blogs, videos, local search and shopping. Their users are susceptible to cross-site scripting (XSS) and phishing attacks, as reported by security researcher Azat Harutyunyan.
Malicious users are able to exploit the XSS vulnerability, allowing them to compromise the security of targeted client computers and consequently whole networks, just by launching a sophisticated phishing attack that is aided by a malicious JavaScript. They could also exploit the allowed frame redirection in order to point phishing victims to a fake Ask.com page and ask them to input sensitive information or download a malicious fake Ask.com toolbar.
Ask.com Frame Redirect/XSS mirrors:
www.ask.com Frame Redirect
city.ask.com Frame Redirect
int.ask.com Frame Redirect
secure.sponsoredlistings.ask.com XSS on SSL page
mws.ask.com XSS
it.ask.com XSS vulnerability notified by XaDoS
Screenshot for Frame Redirect vulnerability:
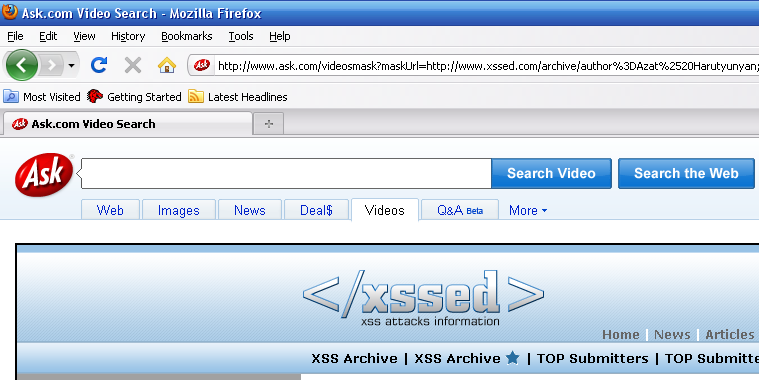
Note: The attack vector can be obfuscated to increase the potential infection/phishing rate.
Screenshot for phishing scenario with fake Ask.com toolbar:
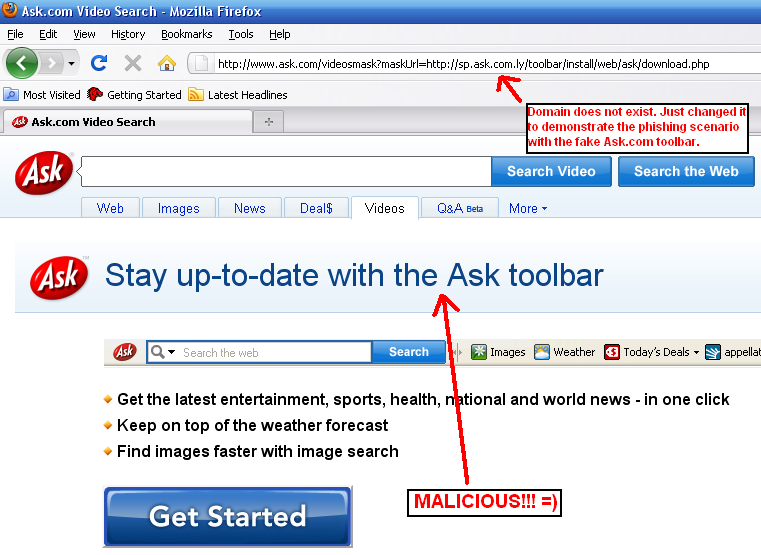
Screenshot for XSS on Ask.com's SSL powered customer login page:
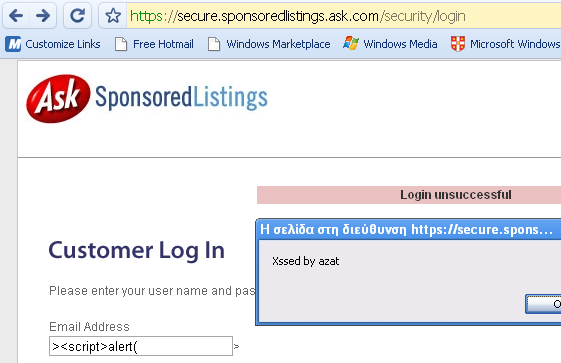
Ask.com sites have been XSSed in the past:
Users should protect against cross-site scripting (XSS) attacks with the following ways:
[1.] Disallow scripting via your browser's settings tab when not required. We recommend that you use Giorgo Maone's NoScript Firefox extension.
[2.] Do not trust links on your e-mail or public forums, especially the suspicious looking ones. It is also wise to always look at carefully at URLs and the URL parameters that are provided with them. URLs will always appear in the status bar of your browser as and you should always look for external script reference.
[3.] Another solution would be to manually type in links into the URL bar of your browser if a link is suspect. HSCBC.com is not the same as HSBC.com.
[4.] Disallow Flash unless you are sure it can be trusted. You can use NoScript for this too.
[5.] Turn off Java when not trusting the destination address.
[6.] Make sure you clear everything regularly from your browser (Cookies, authentication sessions etc).
References:
"Preventing Cross Site Scripting Attacks" - by Nilesh Pawar
| 